💻-🖥️-📱 Anonymously Use Web Services
| TYPE | AUDIENCE | PRIORITY | COMPLEXITY | EFFORT | COST | UPDATED |
|---|---|---|---|---|---|---|
| Conduct | 🧑 | ⭐⭐⭐⭐ | ⭐⭐ | 🧑🧑 | 🆓 | 2021-08-17 |
Rationale
For some private or public-facing activities (such as running a human rights campaign on Facebook), you may not want to attach your name and identity to the activities. Especially in jurisdictions that don't offer strong protections of essential freedoms (e.g. speech, demonstration, petitioning) it may be desirable to be able to anonymous use Web Services like Social Media, Email, or Search.
What you should know
Anonymous vs Pseudonymous
To anonymously use a web service, you need to leave no trace that can identify you between user sessions. So what about services that require you to create accounts and login? Technically, for services that require accounts we are going to use them pseudonymously instead of anonymously .
The difference between being "Anonymous" and "Pseudonymous" is that when you're anonymous there are no traces that can be used to tie activity to the same (unknown) user. For example, a message sent by an 'anonymous' user could actually be sent by anyone! The next time an anonymous user sends a message, the receiver would have no way of knowing it is from the same person - it could again be from anyone! That's because there are no identifiers to link the two messages to the same anonymous user.
If you receive messages from a "Pseudonymous" user however, that user may still be unknown, but their screen name or other identifier is persistent. So if you receive two messages from a pseudonymous user, you can typically assume they were sent by the same user account.
This distinction is important because many web services require you to make an account. Services like Facebook don't allow Anonymous users, only Pseudononymous accounts, so all activity by the registered account will be tracked and associated with that account. That's why it is really important that you never allow Facebook or any other web service to connect your Pseudononymous account to your own personal account.
Who are you hiding from?
To understand what steps are necessary, we need to understand who we are trying to keep our identity concealed from:
- Hackers - Only use trusted devices and networks
- Internet Service Provider (ISP) or Mobile Phone Provider (Telco) - Encrypt your internet traffic
- Web Service Operators - Use burner accounts and isolated browsers
- Web Service Users - Avoid posting revealing data
What you should prepare
We will setup a computer of smartphone with all protection that are available to us, and make a best possible effort to conceal your activities. So let's prepare your devices, network and applications so that they stop leaking your identity.
1. Conceal your activity from Hackers
None of our precautionary methods will have any effect if the devices you are using are compromised - e.g. if adversaries have managed to install monitoring software or keyloggers and are tracking your activity either at the device or local network level (WiFi Access Point or Router).
That is why we recommend to always start from a clean slate when setting up your security so that you can build on top of a strong foundation. In practice this means first resetting your devices to factory settings, then following the relevant guides to secure your devices. Of course, don't forget to back-up any data you don't wish to lose in the reset!
For Computers, at a minimum, reset to factory settings for [Windows]](https://www.pcmag.com/how-to/factory-reset-windows-10) or macOS and:
- Install all available updates
- 💻-🖥️ Windows 10 - Turn on Full Disk Encryption
- 💻-🖥️ Install Antivirus Software
For Smart Devices, at a minimum, reset your Android or iOS device to factory settings and:
- Install all available updates
- 📱 Android - Enable Full-device Encryption
- 📱 Install Apps From Trusted Sources
- 📱 Configure your Lock Screen
In terms of network security - we suggest only connecting to networks you trust (so no public WiFis).
Using a freshly configured device over a trusted network, you can reasonably assume that your devices are not compromised.
2. Conceal your activity from your ISP
To hide your internet activity from your ISP, you need to hide both your DNS Lookups and the actual traffic.
- 💻-🖥️-📱 Setup Cloudflare WARP and then 💻-🖥️-📱 Connect to Cloudflare WARP - your ISP now can no longer see which sites you are visiting, only that you are connecting to CloudFlare's WARP service.
If you are using another VPN service, your traffic is most likely hidden from your ISP, though if you haven't configured your DNS settings it's possible that you are still leaking your DNS lookups each time you visit a site - you can test your device + network configuration by performing a DNS leak test. If the test results don't show your encrypted DNS provider (e.g. Cloudflare at 1.1.1.1, Google Public DNS at 8.8.8.8 and 8.8.4.4, or Comodo at 8.26.56.26 and 8.20.247.20) then you should consider setting one up - for example by using WARP and using the secure DNS mode.
3. Conceal your identity from Web Service Operators
This is probably the hardest step - and the easiest one to make mistakes with - as once your identity has been compromised by a web service like Facebook or Google, they will never forget it.
You may not be worried that e.g. Facebook knows your identity, as you trust that Facebook will not disclose your identity to your adversaries. However, through Facebook's social algorithms it "leaks" aspects of your identity and social network.
For example, if Facebook knows that your personal and "hidden" account belong to the same person, your Friends may be asked whether they "know" your hidden account, even if they don't know you are behind the account. If several of your friends' accounts were compromised, your adversary may use this 'suggested friends' feature to triangulate who the hidden account may actually belong to. You thus don't even ever want Facebook to know that you are the person behind the pseudonymous account.
Similar issues exist for other Web Services. So how do they know who you are? It's because they use a mixture of identifiers to tag and track you:
- Your device model and operating system
- Supported browser features
- Your window and screen sizes
- IP address
- Unique device identifiers
- Cookies
And many other features which are used to "Fingerprint" you. You can test how anonymous your current setup is with EFF's Fingerprint Tester.
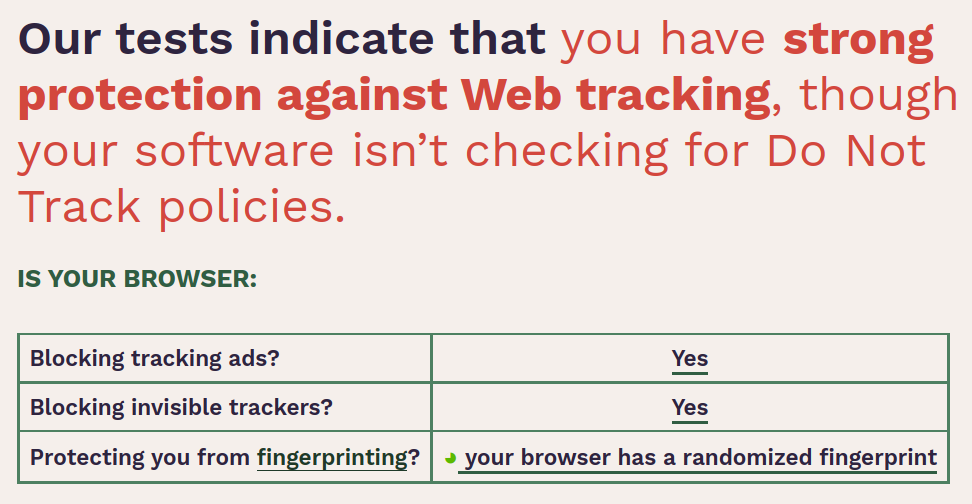
The easiest way to get security against fingerprinting and also protect your IP address from Web Services is to access them over TOR (The Onion Router) Browser:
- 💻-🖥️-📱 Setup a Tor Browser and
- Access the Web Services your want to use anonymously over the TOR Network.
Also keep the following practices in mind to NOT leak any identifiable information to the Web Service:
- Do Not log into multiple accounts in the same browser session - i.e. close the browser before you log into your other account.
- Do Not "engage" with any content you don't need to - i.e. don't "upvote" posts or "like" things
- Do Not build up your social graph - i.e. do not add any of your contacts to your Pseudononymous account
If you're interested in using Facebook anonymously, ensure that your account itself is also secured per the advice from 🌐 Secure a Facebook Account.
4. Conceal your identity from other Web Service Users
If the Web Service you're using has other users you can interact with (e.g. Facebook, Facebook, Reddit), before you post something to the service, ensure that:
- You don't have any identifiable information in the text message. i.e. are not using special phrases that only you use. Stick to standard punctuation and spelling.
- Photos don't show sensitive locations, or faces.